Of Cybercriminals and IP Addresses
You don't like having the FBI knocking on your door at 6 am in the morning. Surprisingly, nor does your usual cybercriminal. That is why they hide (at least the good ones), for example, behind layers of proxies, VPNs, or TOR nodes.
Their IP address will never be exposed directly to the target's machine. Cybercriminals will always use third-party IP addresses to deliver their attacks.
There are countless ways to deliver cyberattacks. But one thing is common to all of them. The need for a pool of IP addresses to serve as a medium. Criminals need IP addresses to deliver distributed denial of service attacks.
Criminals need IP addresses to hide behind when probing services. Criminals need IP addresses to attempt brute force attacks. Criminals need IP addresses to run bot networks and services. In a nutshell, criminals need to maintain IP addresses under their control for pretty much anything. It is their most important asset and is the ammo they need to deliver attacks.
So how do cybercriminals get their hand on those infamous IP addresses, and what does this cost them? Here are some examples.
"admin/admin"
Hijacking machines and more specifically networks of IoT devices. Poorly secured and managed fleets of IoT devices left with default access credentials and outdated firmware are the perfect target for that. Easy way to zombify a large number of devices, freshly served for DDoS attacks…hey "smart" security cameras…we are watching you!
"VPS are cheap"
Take any cloud provider, fire up some instances, install bots to scan & attempt Log4j injections. At a limited cost, you have your bot network to scan targets for vulnerabilities. Of course, at some point, you will get flagged or the provider might catch you. But you can replicate your approach with cloud providers in other countries, maybe less regarding the usage of those VPS…
'Into darkness"
They can also go to the supermarket for criminals, aka. "dark web" and acquire a network of bots to deliver attacks like DDoS for a couple of hundred dollars. Script kiddies, welcome.
Two take-aways from these approaches :
Acquiring IP addresses, although not impossible, costs money, time, and resources. Tamper with that, you tamper with a criminal's ability to do his job efficiently. Ban known IPs used by criminals and you might just drastically increase the security of your online assets.
Those bots and scan automation activities generate a lot of internet background noise. Imagine all those countless botnets scanning the IP space for different nefarious purposes. This is well known by SOC analysts as "alert fatigue", meaning, this generates a large amount of data, without much-added value, but that analysts still need to take into account.
But good news everyone, there are solutions to make life more difficult for cybercriminals.
IP reputation is part of the solution. Suppose users can preventively evaluate the risk of an IP connecting to a service. In that case, it can lock out known malicious users and make sure those IPs can not hurt anyone anymore, de-facto taking away the IP address pool criminals spent time and money to build.
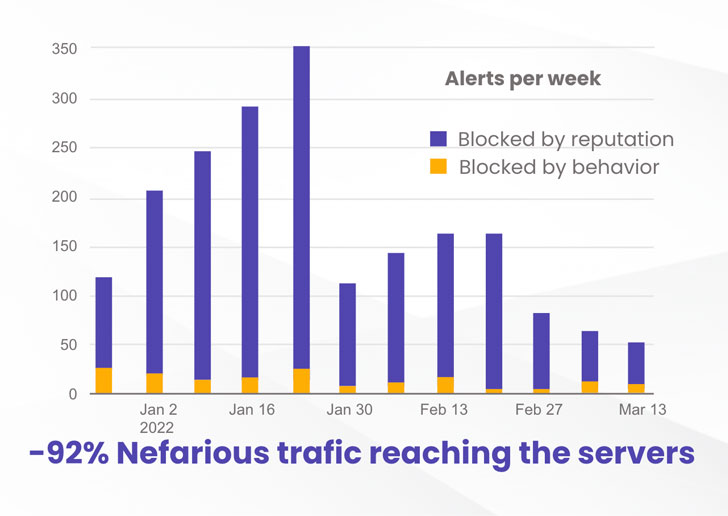
At CrowdSec, we did fun experimenting: we set up two identical VPSs on a well-known cloud provider, with two simple services, SSH and Nginx. Nothing fancy, just like millions of machines out there in the wild. CrowdSec was installed on both to detect intrusion attempts. Still, one machine had the remediation agent (IPS), receiving IP reputation information from the CrowdSec community (daily 1 million signals shared) and preventively banning flagged IPs.
The result was quite stunning.
Thanks to the community blocklist, the machine with the IPS preventively blocked 92% of the attacks compared to the machine without the IPS. That is a notable increase in security level.
You can read more about the methodology and detailed results at: https://crowdsec.net/
 |
| Source: crowdsec.net |
Community IP blocklists - with the previous curation - take care of both challenges.
It cripples criminals by nullifying their IP address pool. They spent time, money, resources to build them, and we, as a community, simply take them away in the blink of an eye. Take that scum!
But it also makes the life of analysts and cybersecurity experts much easier. By preventively blocking those nefarious IPs, the background noise is significantly reduced. We are talking about reducing by 90% the alerts that need to be analyzed by SOC people. That is much more time to focus on more significant alerts and topics. Alert fatigue? - bye-bye.
If you wish to partake in the biggest IP reputation community and hunt nefarious IP addresses while effectively protecting your online assets, join us at crowdsec.net
Security
via https://www.aiupnow.com
noreply@blogger.com (The Hacker News), Khareem Sudlow
