How to Automate Offboarding to Keep Your Company Safe
In the midst of 'The Great Resignation,' the damage from employees (or contractors) leaving an organization might be one of the greatest risks facing IT teams today. The reality is that in the busy enterprise computing environment, user onboarding and offboarding is a fact of daily life.
When employee counts range into the five-figure territory — and entire networks of contractors have to be accounted for as well — it's easy to lose track of who's, literally, coming and going. Oftentimes, there are "offboarding" steps that are forgotten about — disabling or removing the user from Active Directory or IAM is not sufficient as the user may have local credentials on some of the SaaS platforms or other sensitive systems.
Technically speaking, there are ways to automate offboarding using protocols such as SCIM and JIT mapping; however, it requires a high level of maturity in an IT environment and the staff to implement it.
For organizations not implementing SCIM or JIT, offboarded employees may still have local credentials on some of their regularly used SaaS platforms or other sensitive systems. Leaving these users' access in place exposes organizations to unauthorized data access.
When it comes to taking old users off systems - deprovisioning - there are a few best practices that should be borne in mind and followed.
Best Practices in Deprovisioning
Keep an Inventory — It's essential that IT teams keep an up-to-date record, at all times, of all users with access to company systems. A channel of communication with human resources should be established for keeping abreast of events impacting the user inventory such as employee terminations. To be effective from a security standpoint, these systems need to be capable of scrutinizing both internal and external users. The vendor landscape can be constantly shifting.
Always be on the lookout — In addition to keeping track of intended system users, IT teams need to have a capability for user discovery that accounts for the full breadth of systems they may be accessing - both those in legacy environments, like on-premises systems, and in the mushrooming cloud environment.
Rigorous access control — It's imperative that IT teams develop onboarding and offboarding protocols that account for the full extent of privileged employee computing access. If an employee has access to 3 internal systems and 30 cloud-hosted ones, then clearly limiting access to those on-premises will leave a gaping information hole that they will retain access to.
How to Automate the Deprovisioning Process
The meticulous mapping and security work that this process demands from a security team is vast. A SaaS Security Posture Management solution, like Adaptive Shield, can streamline this process — a simple query in Adaptive Shield's user inventory can reveal the user posture of the deprovisioned users' accounts across the entire SaaS stack.
When it comes to deprovisioning these accounts, orchestration tools give security teams an easy way to integrate Adaptive Shield's capabilities into an automated deprovisioning workflow. This vastly simplifies the process, reducing the amount of time it takes to fully deprovision users, and ensuring that no accounts are left active.
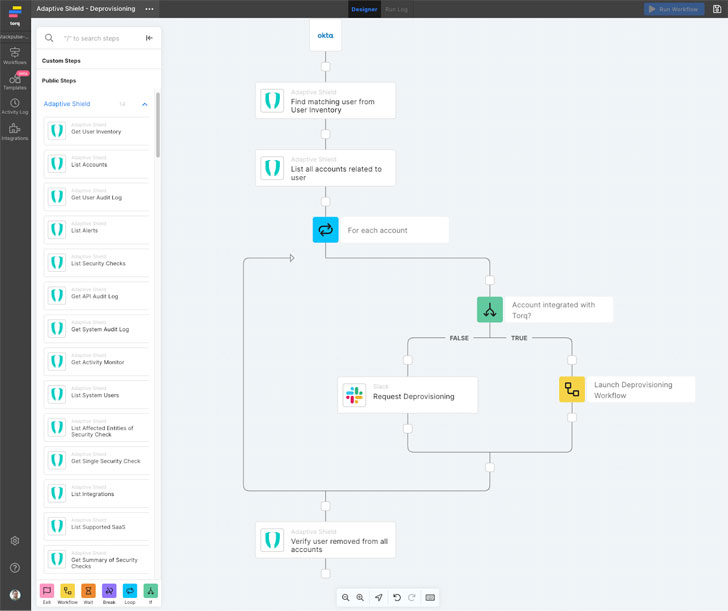 |
| Screenshot provided by Torq |
In the figure above, you can can see a potential workflow where:
- The initial IAM deprovisioning can be used as the hook to notify Adaptive Shield that a deprovisioning event has occurred.
- Adaptive Shield can probe the organization's integrated SaaS landscape for records for that user,
- When Adaptive Shield detects an active account, it triggers a workflow in the automation tool that identifies the account, and deactivates it.
-
- If the account cannot be directly deactivated, it sends a message via Slack to an administrator, asking them to confirm the deactivation.
- The automation tool then re-runs the security check in Adaptive Shield, to verify account deactivation.
This workflow is just one example of how Adaptive Shield's integration with an orchestration tool streamlines the deprovisioning process through automation; not only to ease the burden of manual auditing and deactivating accounts, but also providing continuous visibility and control increasing the organization's SaaS security posture.
Learn more about how to automate deprovisioning for your organization.
Security
via https://www.aiupnow.com
noreply@blogger.com (The Hacker News), Khareem Sudlow
